
 Yes, for the second time in my life. First time it was still in my university years. In those times if you had internet access at home, you were priveleged. Companies were paying quite a lot of money to get a slow 28K dial-up connection, and internet providers were charging per minute, not by gigabyte. I set up access to the university internet connection via modem in our lab – I was running FIDO net node on the same machine. One guy (I later on found him) noticed that there’s a PPP connection attempt before FIDO mail software kicks in and successfully brute forced the password. I should admit that I didn’t bother that much when I was setting the password – it was not the default one, but pretty close. It was quite easy to spot the attack – phone line was busy all the time. What the attacker didn’t know is that the modem I used was a sophisticated US Robotics Sportster model with CallerID detection, so it was rather easy to trace the attacker.
Yes, for the second time in my life. First time it was still in my university years. In those times if you had internet access at home, you were priveleged. Companies were paying quite a lot of money to get a slow 28K dial-up connection, and internet providers were charging per minute, not by gigabyte. I set up access to the university internet connection via modem in our lab – I was running FIDO net node on the same machine. One guy (I later on found him) noticed that there’s a PPP connection attempt before FIDO mail software kicks in and successfully brute forced the password. I should admit that I didn’t bother that much when I was setting the password – it was not the default one, but pretty close. It was quite easy to spot the attack – phone line was busy all the time. What the attacker didn’t know is that the modem I used was a sophisticated US Robotics Sportster model with CallerID detection, so it was rather easy to trace the attacker.
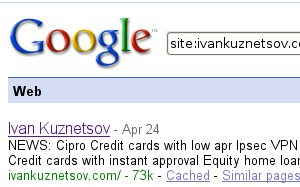
But that was more than 10 years ago. Now I noticed that something is wrong when I started recieving a lot of comment spam from this blog. Captcha plugin was doing an excellent job before, so I decided to check what’s going on. Somehow all plugins were disabled. Re-enabling them solved the problem with comment spam, but then Goolge started generating weird excerpts for ivankuznetsov.com search results. That’s when I started digging deeper and discovered that a hidden div with advertisments was inserted into WordPress PHP scripts.
Dreamhost support was kind enough to point me to the description of the attack that was used to break my blog. This particular problem, as well as some other security issues have been fixed in the latest Word Press release – 2.5.1. Lesson learned – update software on time and make backups.
If you are using WordPress older than 2.5.1 I would recommend you to upgrade ASAP.

Leave a Reply